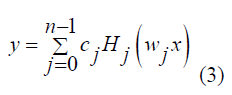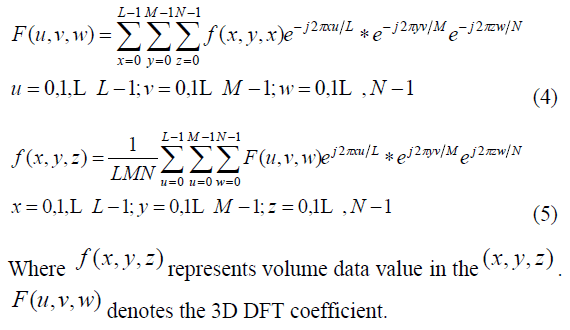Keywords
|
| Medical volume data, watermarking, geometric attacks, Chebyshev chaotic neural network. |
Introduction
|
| With the development of medical imaging technology, as well as the mutual penetration between computer and communication technology and medical imaging, medical imaging plays an increasingly important role in modern medical diagnosis [1,2]. In recent years, with the progress of computer technology, especially the high resolution Computer X optical tomography (CT) and Magnetic resonance imaging (MRI) and advanced optical scanners, such as the emergence of new equipment and a series of related software development, medical images has been considered more and more significant [3,4]. For example, CT and MRI images have higher spatial resolution, which can provide anatomical structure, clear human structure and detailed pathological information [5-6]. It provides a direct and reliable method for clinical medicine and scientific research. Its application scope has gradually covered the preoperative diagnosis, surgical design, postoperative prediction and evaluation of efficacy and so on. But with the Electronic medical record (EPR) and medical image spreaded on the Internet, the information security problem of medical images is gradually exposed [7]. When medical images over the network for remote transmission, the patient's personal information recorded in medical images can easily be leaked [8,9]. Today's encryption method [10] and access control has been not capable to meet the medical information security requirements, so to seek new information security technology measures are imminent. If the personal information is embedded in the medical image as a digital watermarking, the problem can be solved. The watermarking is called medical volume data digital watermarking [11]. |
| At present, there are a few researches on the digital watermarking algorithm of the volume data of anti-geometric attacks [12-14]. The volume data exists in a large number of medical images, such as: medical volume data (CT, MRI volume data) are composed of volume data by the slice. So it is significant to study how to embed digital watermarking in volume data so that medical volume data cannot be modified. This is the difficulty of improving the embedding watermark technique in the volume data. Now medical volume data watermarking can only be resistant to conventional attacks, even for common minor geometric attacks. Therefore, in medical volume data watermarking research fields, geometric attack is still a relatively difficult problem to solve. |
| The research of this paper can be a good solution to the medical volume data information security problems in the current medical field. The particularity of medical volume data is fully considered in this paper. A novel volume watermarking algorithm for medical volume data is brought out. Differences hashing is used to realize the watermarking embedding and extraction of the medical volume data. Before embedding the watermarking, the watermarking is scrambled. It adopts chebyshev chaotic neural network. The watermarking algorithm has good resistance to geometric attacks, and has better security. |
Materials and Methods
|
| Chebyshev chaotic neural network |
| This paper uses a new chebyshev chaotic neural network [15]. The chebyshev chaotic neural network model is shown in figure 1. |
| Definition 1 |
| Chn(x) = cos(n arccos x) (1) |
 |
| Definition 2 |
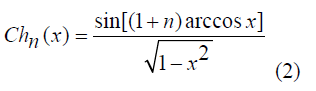 |
| Chn (x) is known as the second-class chebyshev polynomials. |
It is known as the weight function 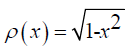 n orthogonal polynomials in space [-1, 1]. n orthogonal polynomials in space [-1, 1]. |
| Chebyshev chaotic neural network output is |
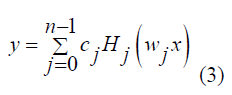 |
| Where first-layer weight is w j , second-layer weight is c j , j = 0,1,2,L ,n .The activation function of hidden layer neuron is chebyshev orthogonal polynomials. Its weight is trained using BP learning algorithm. |
| 3D discrete wavelet transform |
| Wavelet transform is a milestone in the development of signal analysis. In recent years, it has become a hot topic in many disciplines, which is widely used in the fields of image encoding, texture analysis, pattern recognition, and computer vision and so on. Wavelet transform has good localization property in time domain and frequency domain. |
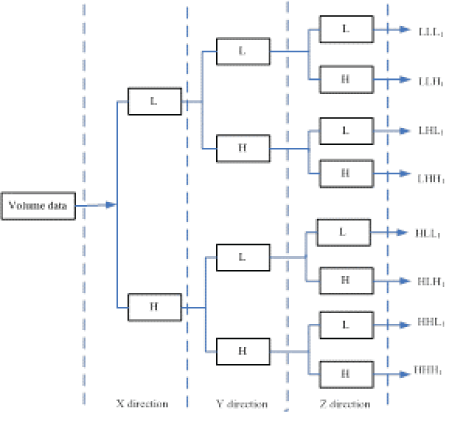
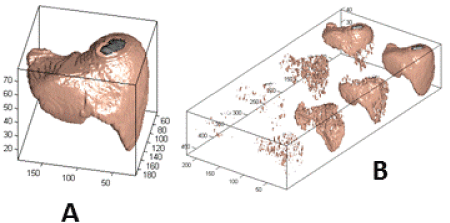
| 3D wavelet transform is an extension of the two-dimensional wavelet transform, which provides the good multi-resolution analysis feature on space for 3D volume data. The decomposition process of the 3D wavelet transform is shown in Figure 2. The medical volume data is shown in Figure 3(a), which is the liver volume data and the Figure 3(b) is 3D wavelets transform. |
| 3D discrete Fourier transform |
| Fourier transform has been a basic mathematical tool in signal processing, especially in spectrum analysis. It can be expressed as the superposition of different frequency wave functions, so that the study of the time domain signal is converted to the frequency domain coefficients. 3D DFT formulas are as shown in formula (4) and formula (5). |
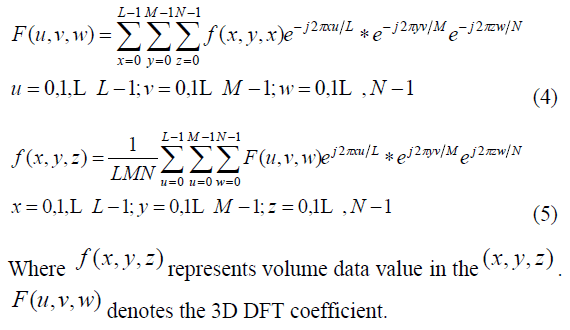 |
| Watermarking algorithm |
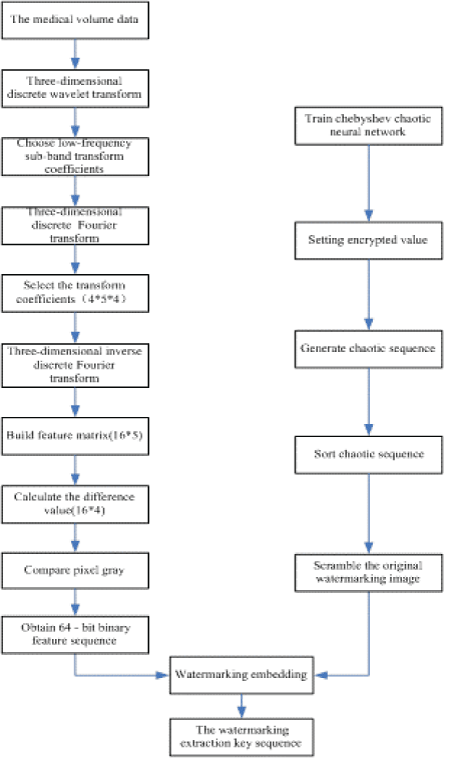
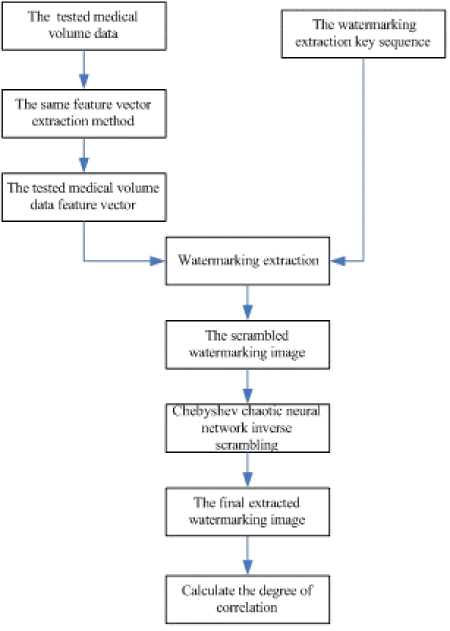
| Watermarking embedding process is shown in Figure 4. Watermarking extraction process is shown in Figure 5. |
Results
|
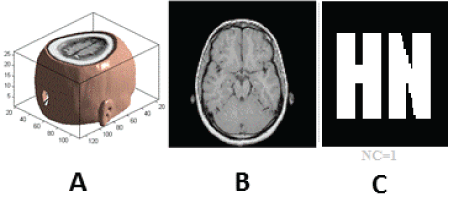
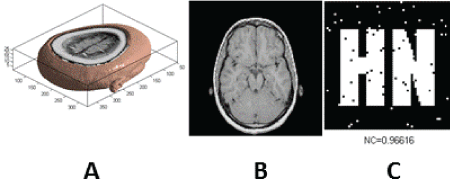
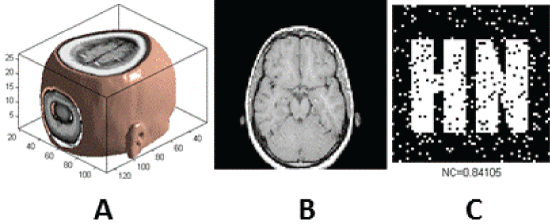
| The watermarking algorithm is implemented in Matlab2010a platform to test and verify the effectiveness. The original medical volume data uses a set of MRI brain data, which contains 27 pieces of the human head slice images (128*128), whose storage format is 128 (pix) × 128 (pix) × 1(bit) × 27 (slices).It is a four-dimensional (4D) image, which needs to be reduced to 3D in order to use. The medical volume data without attack is as shown in Figure 6 (a). The slice is shown in the Figure 6 (b). The extracted watermarking image is shown in the Figure 6(c). At present, the anti-attack ability of the digital watermarking algorithm cannot meet the expected requirements, usually only to the noise, compression and filtering and other attacks have a certain robustness. Especially the research on the digital watermarking algorithm against geometric attacks is not mature enough. |
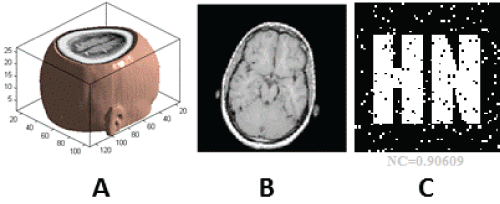
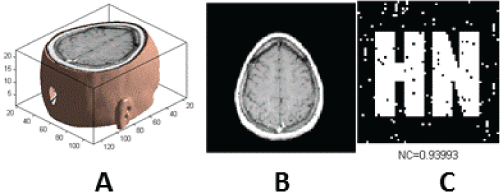
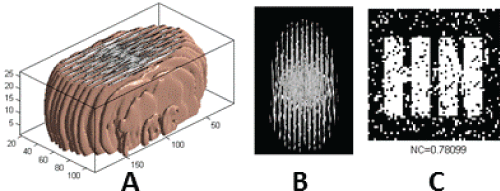
| The salient feature of geometric attacks is that when the image is slightly changed, most of the watermarking detector cannot extract the watermarking information. In order to test the robustness of the proposed watermarking algorithm, the simulation experiments are carried out by the following geometric attacks. The specific attack experiments are as follows. Figure 7 give experimental results under zooming attack. Experimental results under clockwise rotation attack are shown in Figure 8. Figure 9 describe experimental results under shear attack. Figure 10 show experimental results under distortion attack. Experimental results under translation attack are depicted in Figure 11. As it can be seen from the figures, the extracted watermarking images are very clear. Hence, the proposed watermarking algorithm has a strong robustness to anti-geometric attacks. |
Discussion
|
| At present, most of the medical images watermarking algorithms are based on two-dimensional image. According to the capacity and the robustness of the requirement, the different watermarking algorithms are selected. With the development of computer graphics, more and more medical workers pay attention to the research of 3D medical volume data. So the watermarking for 3D medical volume data is very essential. The proposed watermarking algorithm is applied to the 3D medical volume data. The proposed watermarking algorithm was compared with the algorithms in the [16,17]. These techniques are also given in Table 1. Can be seen from Table 1, the proposed watermarking algorithm, Guoyan Liu [16] and Memon [17]’s watermarking algorithm are robust watermarking algorithm. However, the research object of the proposed watermarking algorithm is 3D medical volume data. The object of the Guoyan Liu [16] and Memon’s [17] watermarking algorithms are the two-dimensional (2D) medical image. The proposed watermarking algorithm and the [16,17] experimental results indicate that each robust watermarking algorithm has good robustness and security, and can very good solve a variety of medical image information security problems. However, the embedding watermarking significantly changes the contents of medical images, which will affect the doctor's diagnosis [16,17]. The proposed watermarking algorithm is zero-watermarking algorithm, which make any changes to the original medical volume data, will not affect the doctor's diagnosis. Experimental results show that the proposed watermarking algorithm was better robustness and security, which would play a role in the protection of medical volume data. Therefore, the proposed watermarking algorithm is more practical in the field of medical research. |
Acknowledgements
|
| This work was supported by the National Natural Science Foundation of China (No. 61263033), the International Science and Technology Cooperation Project of Hainan (No.KJHZ2015-4), the Higher School Scientific Research Project of Hainan Province (No. Hnky2015-80) ,the Institutions of Higher Learning Scientific Research Special Project of Hainan (Hnkyzx2014-2) and the Higher School Outstanding Young Backbone Teachers Funded Project of Hainan Province (No: 2014-129). |
Tables at a glance
|
 |
| Table 1 |
|
Figures at a glance
|
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
 |
 |
 |
 |
| Figure 5 |
Figure 6 |
Figure 7 |
Figure 8 |
 |
 |
 |
| Figure 9 |
Figure 10 |
Figure 11 |
|
References
|
- Reiner BL, Siegel EL, Henper F. Impact of film less imaging on the frequency of clinician review of radiology images. J Digit Imaging 1998; 11: 3-7.
- Hailian LV, Wenfeng X, Yibo Z, Fawei J. Application experience of medical image archiving and communication system. J Pract Med 2004; 5: 230-231.
- Al-QershiOM, Khoo BE.Authentication and data hiding using a hybrid ROI-based watermarking scheme for DICOM images. J Digit Imaging 2011; 24: 114-125.
- He ZW, Lu W, Sun W, Huang JW. Digital image splicing detection based on Markov features in DCT and DWT domain. Pattern Recogn 2012;45: 4292-4299.
- Osamah M, Al-Qershi, Khoo BE. Authentication and data hiding using a reversible ROI-based watermarking scheme for DICOM images. WASET 2009; 50:801-806.
- Dhouib D, Nait-Ali A, Olivier C. Performance evaluation of wavelet based coders on brain MRI volumetric medical datasets for storage and wireless transmission.IntJ Biol Med Sci2008; 3: 147-156.
- Zhang S, Gao T, Gao L.A novel encryption frame for medical image with watermark based on hyper chaotic system. Math ProblEng2014; 1-11.
- Memon NA, ChaudhryA, Ahmad M. Hybrid watermarking of medical images for ROI authentication and recovery.IntJ Comput Math 2011; 88: 2057- 2071.
- Al-Haj A, Amer A. Secured telemedicine using region-based watermarking with tamper localization. J Digit Imaging 2014; 27:737-750.
- Fu C, Meng WH, Zhan YF, Zhu ZL, Lau FC. An efficient and secure medical image protection scheme based on chaotic maps.ComputBiol Med 2014; 43: 1000-1010.
- Seenivasagam V, Velumani R. A QR code based zero-watermarking scheme for authentication of medical images in teleradiology cloud.Comput Math Method M 2013; 4: 1-13.
- Deng X, Chen Z, Zeng F, Zhang Y, Mao Y. Authentication and recovery of medical diagnostic image using dual reversible digital watermarking. J NanosciNanotechnol 2013; 13:2099-2107.
- Kaur M. KAUR R: Reversible watermarking of medical images authentication and recovery-a survey. J InfOperManag2012; 3:241-244.
- Keyvanpour MR, Merrikh-Bayat F. Robust dynamic block-based image watermarking in DWT domain. ProcediaComput Sci.2011; 3:238-242.
- Wang LD, Duan MT, Duan SK.Memristivechebyshev neural network and its applications in function approximation. Math ProblEng 2013; 1-8.
- Guoyan L, Hongjun L, Abdurahman K.Wavelet-Based color pathological image watermark through dynamically adjusting the embedding intensity.Comput Math Methods Med2012;1-11.
- Memon NA, Gilani SAM, Ali A. Watermarking of chest CT scan medical images for content authentication.Int J Comput Math 2010; 88:265-280.
|

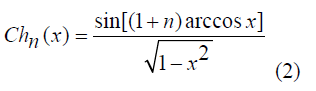
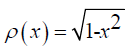 n orthogonal polynomials in space [-1, 1].
n orthogonal polynomials in space [-1, 1].